写在前面
英文好的直接看原文:https://github.com/yivo/docker-centos7-openvpn
原生安装的方式非常麻烦,涉及很多证书方面的知识,尝试了一次无法连接,因此推荐使用docker方式安装
第一步 设置初始环境变量
如果不能使用80端口,则需要修改OPENVPN_SERVER_PORT
全文需要手动修改的只有这一步,其余步骤只需要复制,粘贴执行即可
export OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH="/etc/openvpn"
export OPENVPN_SERVER_IP=$(curl http://ipecho.net/plain)
export OPENVPN_SERVER_PORT="80"
export OPENVPN_SERVER_PROTOCOL="udp"
export OPENVPN_SERVER_NAME="${OPENVPN_SERVER_PORT}${OPENVPN_SERVER_PROTOCOL}"
export OPENVPN_SERVER_HOME_DIRECTORY_PATH="${HOME}/openvpn_${OPENVPN_SERVER_NAME}"
export OPENVPN_SERVER_CIPHER="AES-128-GCM"
export RSA_KEY_SIZE="2048"
export DH_KEY_SIZE="2048"
export EASY_RSA_ROOT="${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/EasyRSA-3.1.0"修改2,3行(根据自身实际情况修改):
export OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH="/etc/openvpn"
export OPENVPN_SERVER_IP=192.168.131.81
export OPENVPN_SERVER_PORT="1194"
export OPENVPN_SERVER_PROTOCOL="udp"
export OPENVPN_SERVER_NAME="${OPENVPN_SERVER_PORT}${OPENVPN_SERVER_PROTOCOL}"
export OPENVPN_SERVER_HOME_DIRECTORY_PATH="${HOME}/openvpn_${OPENVPN_SERVER_NAME}"
export OPENVPN_SERVER_CIPHER="AES-128-GCM"
export RSA_KEY_SIZE="2048"
export DH_KEY_SIZE="2048"
export EASY_RSA_ROOT="${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/EasyRSA-3.1.0"第二步 在本机创建目录
继续执行
mkdir -p ${OPENVPN_SERVER_HOME_DIRECTORY_PATH}
mkdir -p ${OPENVPN_SERVER_HOME_DIRECTORY_PATH}/configuration第三步 拉取openvpn容器,并进入容器中
docker run \
-it \
--rm \
--mount type=bind,source=${OPENVPN_SERVER_HOME_DIRECTORY_PATH}/configuration,target=${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH} \
eahome00/centos7-openvpn:2.5.7 \
/bin/bash -l拉取镜像完成后会自动进入容器

第四步 在容器中设置环境变量
将第一步的环境变量重新在容器中导入一次
export OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH="/etc/openvpn"
export OPENVPN_SERVER_IP=192.168.131.81
export OPENVPN_SERVER_PORT="1194"
export OPENVPN_SERVER_PROTOCOL="udp"
export OPENVPN_SERVER_NAME="${OPENVPN_SERVER_PORT}${OPENVPN_SERVER_PROTOCOL}"
export OPENVPN_SERVER_HOME_DIRECTORY_PATH="${HOME}/openvpn_${OPENVPN_SERVER_NAME}"
export OPENVPN_SERVER_CIPHER="AES-128-GCM"
export RSA_KEY_SIZE="2048"
export DH_KEY_SIZE="2048"
export EASY_RSA_ROOT="${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/EasyRSA-3.1.0"第五步 生成证书
# Download Easy RSA and unpack to /etc/openvpn/easy-rsa.
curl -sL https://github.com/OpenVPN/easy-rsa/releases/download/v3.1.0/EasyRSA-3.1.0.tgz | tar xz -C ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}
# Populate Easy RSA vars.
echo "set_var EASYRSA_KEY_SIZE ${RSA_KEY_SIZE}" > ${EASY_RSA_ROOT}/vars
# Create the PKI, set up the CA, the DH params and the server + client certificates.
cd ${EASY_RSA_ROOT}
./easyrsa init-pki
rm -f vars
./easyrsa --batch build-ca nopass
openssl dhparam -out dh.pem ${DH_KEY_SIZE}
EASYRSA_CERT_EXPIRE=3650 ./easyrsa build-server-full server nopass
EASYRSA_CERT_EXPIRE=3650 ./easyrsa build-client-full client nopass
EASYRSA_CRL_DAYS=3650 ./easyrsa gen-crl
# Generate TLS authentication key.
openvpn --genkey secret ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/tls-auth.key
# Copy all the generated files to /etc/openvpn.
cp pki/ca.crt \
pki/private/ca.key \
dh.pem \
pki/issued/server.crt \
pki/private/server.key \
pki/crl.pem \
${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}上面命令中生成证书的操作openssl dhparam -out dh.pem ${DH_KEY_SIZE}0耗时较长,请耐心等待,我就等待了10分钟。
第六步 生成openvpn server端配置
# Generate server configuration file.
cat > ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/server.conf << EOF
port ${OPENVPN_SERVER_PORT}
proto ${OPENVPN_SERVER_PROTOCOL,,}4
dev tun
user nobody
group nobody
persist-key
persist-tun
keepalive 10 120
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "dhcp-option DNS 1.0.0.1"
push "dhcp-option DNS 1.1.1.1"
push "redirect-gateway def1 bypass-dhcp"
crl-verify crl.pem
ca ca.crt
cert server.crt
key server.key
tls-auth tls-auth.key 0
dh dh.pem
auth SHA256
cipher ${OPENVPN_SERVER_CIPHER}
data-ciphers ${OPENVPN_SERVER_CIPHER}
tls-server
tls-version-min 1.2
tls-cipher TLS-ECDHE-RSA-WITH-AES-128-GCM-SHA256
verb 3
duplicate-cn
EOF
if [[ "${OPENVPN_SERVER_PROTOCOL}" = "udp" ]]; then
echo "explicit-exit-notify" >> ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/server.conf
fi第七步 生成openvpn client端配置
# Generate client configuration file.
cat > ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/client.ovpn << EOF
client
proto ${OPENVPN_SERVER_PROTOCOL,,}4
remote ${OPENVPN_SERVER_IP} ${OPENVPN_SERVER_PORT}
dev tun
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA256
auth-nocache
cipher ${OPENVPN_SERVER_CIPHER}
tls-client
tls-version-min 1.2
tls-cipher TLS-ECDHE-RSA-WITH-AES-128-GCM-SHA256
ignore-unknown-option block-outside-dns
setenv opt block-outside-dns
verb 3
<ca>
$(cat ${EASY_RSA_ROOT}/pki/ca.crt)
</ca>
<cert>
$(cat ${EASY_RSA_ROOT}/pki/issued/client.crt)
</cert>
<key>
$(cat ${EASY_RSA_ROOT}/pki/private/client.key)
</key>
key-direction 1
<tls-auth>
$(cat ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/tls-auth.key)
</tls-auth>
EOF
if [[ "${OPENVPN_SERVER_PROTOCOL}" = "udp" ]]; then
echo "explicit-exit-notify" >> ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/client.ovpn
fi第八步 生成openvpn server 启动脚本
cat > ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/server.sh << EOF
#!/bin/sh
# Create TUN/TAP device if it doesn't exist.
# See https://groups.google.com/d/msg/docker-user/2jFeDGJj36E/XjFh5i1ARpcJ
mkdir -p /dev/net
[ ! -c /dev/net/tun ] && mknod /dev/net/tun c 10 200 && chmod 600 /dev/net/tun
# Check TUN/TAP device. It should output "cat: /dev/net/tun: File descriptor in bad state" and exit with code 1.
cat /dev/net/tun || true
# Enable and configure NAT.
iptables -t nat -C POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE 2>/dev/null || {
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
}
openvpn --config ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/server.conf --cd ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}
EOF第九步 设置文件权限
chown -R root:root ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}
chmod -R 600 ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}
chmod 755 ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}
chmod 700 ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/server.sh
touch ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/ipp.txt
chown nobody:nobody ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/ipp.txt
chmod 660 ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/ipp.txt
chown nobody:nobody ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/crl.pem
chmod 400 ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/crl.pem第十步 退出openvpn容器
退出容器ctrl + c 或者 输入exit命令
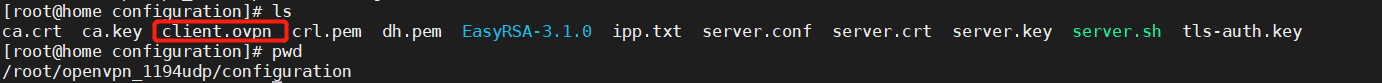
第十一步 在文件系统中获取client.ovpn文件
复制client.ovpn,默认位置:/etc/openvpn-80UDP/client.ovpn
根据第一步环境变量配置不同,文件的目录也不同,我的配置文件目录在/root/openvpn_1194udp/configuration
第十二步 对宿主机相关配置进行设置
cat >> /etc/sysctl.d/99-openvpn.conf << EOF
net.core.default_qdisc=fq
net.ipv4.tcp_congestion_control=bbr
net.ipv4.ip_forward=1
net.ipv6.conf.all.disable_ipv6=1
net.ipv6.conf.default.disable_ipv6=1
net.ipv6.conf.lo.disable_ipv6=1
EOF
sysctl --system第十三步 开启docker服务
前台启动
docker run \
-it \
--rm \
--cap-add=NET_ADMIN \
--mount type=bind,source=${OPENVPN_SERVER_HOME_DIRECTORY_PATH}/configuration,target=${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH},readonly \
-p 0.0.0.0:${OPENVPN_SERVER_PORT}:${OPENVPN_SERVER_PORT}/${OPENVPN_SERVER_PROTOCOL} \
--name openvpn_${OPENVPN_SERVER_NAME} \
--log-driver=json-file \
--log-opt max-size=8M \
--log-opt max-file=1 \
eahome00/centos7-openvpn:2.5.7 \
${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/server.sh后台启动
docker run \
-d \
--restart=unless-stopped \
--cap-add=NET_ADMIN \
--mount type=bind,source=${OPENVPN_SERVER_HOME_DIRECTORY_PATH}/configuration,target=${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH},readonly \
-p 0.0.0.0:${OPENVPN_SERVER_PORT}:${OPENVPN_SERVER_PORT}/${OPENVPN_SERVER_PROTOCOL} \
--name openvpn_${OPENVPN_SERVER_NAME} \
--log-driver=json-file \
--log-opt max-size=8M \
--log-opt max-file=1 \
eahome00/centos7-openvpn:2.5.7 \
${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/server.sh开启docker-compse服务(可选操作)
生成docker-compse配置文件
cd ${OPENVPN_SERVER_HOME_DIRECTORY_PATH}
cat > docker-compose.yaml << EOF
version: "3.9"
services:
server:
image: eahome00/centos7-openvpn:2.5.7
command: "${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}/server.sh"
restart: unless-stopped
cap_add:
- NET_ADMIN
ports:
- ${OPENVPN_SERVER_PORT}:${OPENVPN_SERVER_PORT}/${OPENVPN_SERVER_PROTOCOL}
volumes:
- type: bind
source: ./configuration
target: ${OPENVPN_SERVER_CONFIGURATION_DIRECTORY_PATH}
logging:
driver: json-file
options:
max-size: 8MB
max-file: "1"
EOF使用docker-compose拉起镜像
docker-compose up -dwindows端openvpn连接
下载地址
https://openvpn.net/community-downloads/
客户端配置
在文件夹中指定client.ovpn文件所在目录
点击连接即可,连接成功后,即可访问内网

客户端请求路由配置
上面生成的client.ovpn文件会导致所有的请求都走vpn隧道,我的需求是只有192.168开头的走vpn隧道,修改client.ovpn文件如下
注释掉setenv opt block-outside-dns
添加route-nopull
添加route 192.168.0.0 255.255.0.0 vpn_gateway
#setenv opt block-outside-dns
route-nopull
#以下路由根据自己实际情况进行添加调整
route 192.168.0.0 255.255.0.0 vpn_gateway上述配置的解释文档:https://blog.csdn.net/joshua317/article/details/120245443
